The tempo at which technological developments are going down, the situations of refined assaults are rising the identical means. The dynamic nature of the digital world and the fixed evolution of threats make it essential to implement a slew of preventive measures in the end. The upsurge in cybersecurity threats weakens the integrity of knowledge, programs, and networks, highlighting the importance of vigilance for each companies and people. Thus, the query arises, find out how to cope with cyberattacks successfully? Nicely, we are going to talk about some cybersecurity finest practices for companies on this weblog to deal with widespread assaults in 2025.
Why is Software program Safety Essential for Companies?
Software program safety is a rising concern within the digital age. Cyber threats are fairly superior and require the very best safety to verify of the whole safety of knowledge for compliance and buyer belief. Poor software program safety brings in severe repercussions, together with:
- Monetary losses from information breaches
- Theft of delicate information
- Operational disruptions
- Potential authorized penalties
This might additional result in broken reputations of firms, misplaced buyer belief, and aggressive drawback experiences. In excessive circumstances, the influence might prolong to enterprise shutdown as effectively. Understanding these dangers highlights the significance of implementing prime cybersecurity developments in 2025 to safe property and guarantee long-term success.
The perfect enterprise cybersecurity practices in 2025 defend your model’s picture and are vital for undertaking success in in the present day’s technology-powered market. Now, it’s time to see why incorporating software program safety measures into your product lifecycle means enterprise success.
- Ensures Your Enterprise Continuity: Adopting cybersecurity finest practices for companies makes certain of a seamless operation with out interrupting any actions due to cyber assaults.
- Prevents Your Monetary Losses: The cybersecurity measures additionally scale back the danger of breaches which means no must pay appreciable restoration and remediation prices.
- Maintains Your Buyer Belief: Implementing confirmed cybersecurity ideas for companies helps safeguard buyer information and privateness to develop and keep their confidence.
- Complies with Key Rules: Embracing cybersecurity measures unconditionally helps meet authorized and business requirements, eliminating the scope for hefty fines and authorized penalties.
- Enhances Your Aggressive Benefit: Such measures present a dedication to safety, bettering the attraction of your enterprise to security-conscious prospects.
- Protects Your Repute: Integrating important cybersecurity measures in 2025 protects your model in situations the place there are revealed safety incidents, together with however not restricted to information breaches or ransomware assaults.
- Helps Your Innovation: Incorporating cybersecurity finest observe assists in safe software program improvement and deployment of recent functionalities and applied sciences with out tampering with safety.
- Strengthens Your Safety Structure: These practices assist enhance your general safety structure via safety built-in into every section of the software program improvement life cycle, permitting stable protection in opposition to threats.
- Mitigates Your Dangers: Leveraging cybersecurity finest practices for companies helps establish and resolve potential safety vulnerabilities earlier than they are often misused.
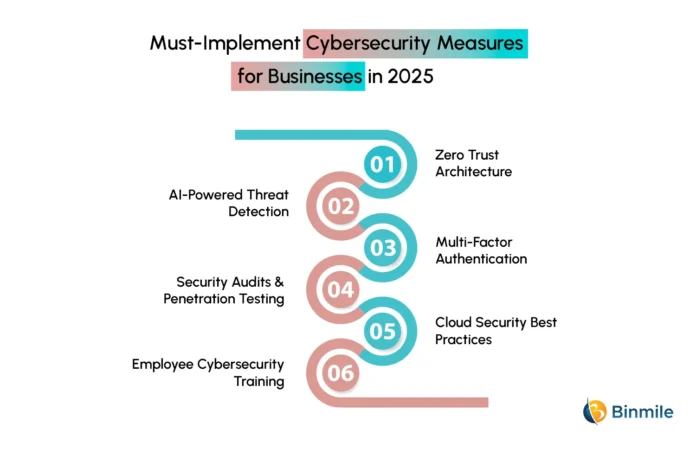
5 Cybersecurity Greatest Practices for 2025 You Should Know
Leveraging important cybersecurity measures in 2025 is extraordinarily vital for companies and a strategic precedence to guard delicate information and keep operational resilience. Sift via 5 principal measures to strengthen your enterprise in opposition to potential cyberattacks.


1. Zero Belief Structure
As of late organizations perceive the challenges of the cyber world and have changed the standard safety mannequin with a brand new strategy, i.e., often known as Zero Belief Structure. It’s cropping up as a necessity, the place belief is rarely presumed. Relatively, each consumer, machine, and software attempting to entry a community useful resource is constantly verified and authenticated, regardless of their location – inside or outdoors the community. By separating entry and making use of the concept of minimal privilege, organizations can mitigate the assault floor and scale back lateral motion inside their programs.
Zero Belief incorporates effectively with the cloud ecosystem, making it a versatile, future-proof, and confirmed cybersecurity techniques for 2025. This is likely one of the principal functions of cybersecurity in enterprise, because it helps companies ensure that every consumer and machine, no matter location, is constantly verified and authenticated previous to accessing sources.
2. AI-Powered Risk Detection
AI-powered risk detection is a kind of cybersecurity finest practices for companies i.e., vital for staying forward within the competitors with fast decision. AI programs analyze community site visitors, acknowledge patterns, and be taught from previous assaults to proactively establish and scale back threats in real-time.
By making the most of machine studying and deep studying algorithms, these programs change into smarter over time, recognizing slight abnormalities that human analysts would possibly skip. AI improves risk detection and incident response, enabling predictive evaluation of potential vulnerabilities and ensuring companies can neutralize dangers earlier than they flip into full-fledged assaults.
3. Multi-Issue Authentication
Within the age of frequent password breaches, relying on passwords alone is extraordinarily dangerous. MFA provides a big layer of protection by requiring customers to supply a number of types of verification previous to having access to delicate programs. This would possibly comprise a mixture of passwords, biometrics, and device-based tokens. Even when a password is leaked, attackers will want a secondary verification kind to get desired entry. Multi-factor authentication is a straightforward but highly effective software to guard in opposition to unauthorized entry and is a key requirement for safeguarding worthwhile enterprise information in 2025. In case, you wish to combine this characteristic into your software, do join with the software program improvement firm now.
4. Safety Audits & Penetration Testing
Staying safe shouldn’t be about adopting a static resolution however steady enhancement and vigilance. Common safety audits ensure that organizations should not solely sticking to business requirements but in addition recognizing and resolving any potential vulnerabilities of their programs. Penetration testing or moral hacking permits companies to mimic real-world assaults, rendering deep insights into weak factors that might be misused by malicious actors. By repeatedly updating these cybersecurity finest practices for companies, organizations in 2025 can keep forward of refined threats, adapt to regulatory modifications, and ensure their defenses are resilient in opposition to fashionable cyber dangers.
5 . Cloud Safety Greatest Practices
With extra firms shifting to the cloud, defending cloud environments will change into extraordinarily vital in 2025. Cloud safety finest practices for stopping cyberattacks comprise, securing cloud configurations, encrypting information, implementing identification and entry administration controls, and making the most of automation to research cloud infrastructure repeatedly. On this shared accountability mannequin, cloud service suppliers and companies should work in tandem to safeguard information, apps, and providers. Organizations additionally must take into consideration potential misconfigurations, which is the principle cause for cloud breaches.
Making use of sturdy cloud safety protocols will safeguard information integrity, availability, and confidentiality, selling a safe digital transformation whereas incorporating cybersecurity ideas for companies into each day practices. As extra companies shift to the cloud and embrace IoT gadgets, the assault floor continues to enlarge. As per an actionable insight-delivering agency, greater than 95% of recent digital workloads might be deployed on cloud platforms by the tip of 2025 and IoT gadgets will exceed 32 billion globally. Whereas cloud service suppliers render highly effective safety features, the complexity of securing varied cloud platforms infuses vulnerabilities, particularly when configurations should not managed correctly.
Able to strengthen your cybersecurity? See how our ML improvement providers can improve your safety technique and defend your enterprise from future threats!


Greatest Cybersecurity Instruments and Practices 2025
1. Wireshark


Wireshark is an open-source console-centric software utilized to observe community protocols. Cybersecurity engineers leverage it to guage community safety weaknesses by repeatedly capturing and monitoring information packets.
Key Options:
- Compatibility throughout varied platforms, like Home windows, Linux, FreeBSD, OS X, and so forth.
- Open-source structure with quite simple integration
- A number of networks and a number of output codecs are supported by decryption protocol helps
- Knowledge is recorded and analyzed in real-time, facilitating fashionable functions safety
2. Nmap


Nmap is a free and open-source cybersecurity software that checks IT programs and networks to find safety vulnerabilities. Additional, it permits software program engineers to trace host uptime, establish potential areas of assaults on the community and repair, and take needed safety actions as and when required.
Key Options:
- Community Mapper is suitable with all well-known working programs, which implies constructing a sustainable Android app safety system is a breeze with this software
- Presents an in-depth overview of the actions of the community on a single dashboard, like hosts which are joined with the community, kinds of packet filters and firewalls deployed to maintain the community safe, the OS it operates on, and so forth
- Regardless of the scale of the community, it permits consultants to search for vulnerabilities on the net
3. Metasploit


Metasploit has experience in penetration testing. It covers all kinds of safety aims, like designing methods to boost the enterprise’s cybersecurity defenses and discovering vulnerabilities in programs and networks, amongst others.
Key Options:
- Assessments system safety of cloud-based functions, servers, networks, and so forth
- Supplies the flexibility to see the slightest rising weaknesses and presents high-level safety 24/7, together with fashionable app safety resilience
- Helps assess and improve IT infrastructure safety in opposition to vulnerabilities reported beforehand
- Appropriate with a myriad of various programs, comprising cloud-based functions, networks, and servers, amongst others
4. Sprinto


Sprinto is a cybersecurity and compliance automation software that performs utterly automated checks on the lowest potential degree to verify of immensely tight safety throughout features. It helps take a look at safety gaps and implement controls to resolve them.
Key Options:
- Create, edit, and handle consumer entry privileges to discourage unauthorized entry and strengthen important cybersecurity measures 2025
- Make sure that of the implementation of controls, akin to firewalls, antivirus, encryption, and extra with real-time management monitoring of key infrastructure
- Handle and report endpoint machine security with Sprinto’s built-in MDM software – Dr Sprinto
- Validate safety and compliance well being from a central dashboard with an instantaneous snapshot of go, fail, due, and important checks
How Can Binmile Fortify High Safety Practices to Defend Companies 2025?
Managing cybersecurity for a corporation shouldn’t be a bit of cake. You want a serving to hand to construct stable mitigation methods to maintain your enterprise working securely. Thus, your seek for that serving to hand concludes at Binmile. As a devoted machine studying improvement firm, we focus on growing bespoke cybersecurity options that swimsuit your enterprise wants, guaranteeing the very best safety in your worthwhile information. At Binmile, we prioritize your cybersecurity wants by delivering custom-made options that strengthen your defenses in opposition to rising threats. Under are the pointers that differentiate us from others:
- All-inclusive Safety Assessments: We deeply assess your current framework to acknowledge vulnerabilities and construct custom-made methods.
- Worker Coaching and Consciousness: We promote a tradition of cybersecurity hygiene by coaching cybersecurity finest practices for companies.
- Superior Risk Detection and Response: We leverage Synthetic Intelligence and Machine Studying for real-time monitoring and quick breach response.
- Belief and Reliability: We have now a confirmed observe report in defending digital property, ensuring your safety wants are fulfilled with perfection.
- Specialization in Safe App Growth: We incorporate safety protocols all through the software program improvement lifecycle for highly effective safety.
Join with us to strengthen your cybersecurity technique and create a resilient framework that helps your enterprise progress whereas conserving cyber threats in test.
Take your cybersecurity to the following degree with our ML improvement providers! We may help you detect threats sooner and predict vulnerabilities simply.


The Rundown
As we enter 2025, the cybersecurity ecosystem will expertise the rise of AI-powered assaults, the rising risk of quantum computing, and the rising vulnerability of social media websites. To remain forward of such challenges, companies must put money into AI-backed defenses, undertake a Zero Belief strategy, and combine internet app authentication. Along with that, firms should put together for a stringent regulatory atmosphere and the upsurging want for cyber insurance coverage. With cybercrime surging at an unprecedented tempo, companies that fail to adapt to threat are extremely more likely to change into the following sufferer. Now’s the time to take a plunge, defend digital property, and safe the long run with the assistance of a famend AI improvement firm.