In at the moment’s digital world, providers for software program safety testing are essential for each enterprise. We at Binary Informatics, a high safety testing firm, know that protecting your digital belongings protected is a should. It helps to construct belief together with your prospects and retains your small business operating easily. Our detailed information explores software program safety testing. It exhibits how these providers can shield your purposes and knowledge from potential threats.
We’ll have a look at the principle components of safety testing providers. This consists of penetration testing and software safety testing. Our information exhibits you the total safety testing course of. It begins with the primary evaluation and ends with the ultimate report. We may also speak in regards to the instruments and applied sciences utilized in software program safety testing. Plus, we’ll point out the challenges companies face when making an attempt to arrange sturdy safety from completely different angles. By the top of this information, you’ll know the right way to decide the appropriate safety testing associate. Additionally, you will be taught the most effective practices to maintain your software program protected in a continuously altering menace panorama.
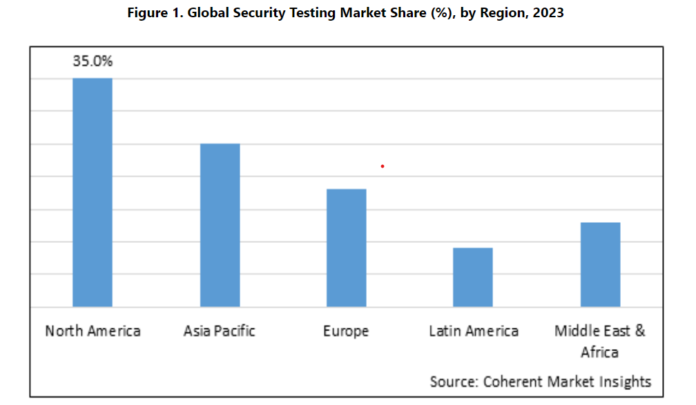
Safety Testing Market Outlook (2023-2030)
Safety testing instruments and providers are used to establish vulnerabilities, threats, dangers in software program purposes, networks, and units. The principle forms of safety testing are static software safety testing, dynamic software safety testing, community safety testing, and social engineering. The rising quantity and class of cyberattacks are driving the necessity for extra in depth safety testing options.
The safety testing market is segmented based mostly on testing sort, deployment mode, group dimension, vertical, and area. By testing sort, the market is segmented into static software safety testing, dynamic software safety testing, cellular software safety testing, and others. Dynamic software safety testing is anticipated to account for the most important market share through the forecast interval owing to its capability to detect vulnerabilities in operating purposes.
Understanding Software program Safety Testing
At Binary Informatics, we perceive that safety testing is essential within the software program growth course of. This can be a methodology that checks the protection of a system or software. It helps discover weaknesses, risks, and dangers. Our manner of doing safety testing makes positive your software program code is protected from potential cyber threats. This protects your essential knowledge and retains the belief of your stakeholders.
Forms of Safety Testing
We use completely different sorts of safety testing to maintain your software program protected and guarded.
- Vulnerability Scanning: That is how we first shield your system. We use automated instruments to search out recognized safety issues, lacking updates, and weak setups in your system.
- Penetration Testing: Our staff pretends to be attackers to search out dangers that our scans might overlook. This helps us see how your system would react to actual threats.
- Threat Evaluation: We discover and rank potential dangers to your group or mission. This lets us concentrate on a very powerful areas.
- Safety Audits: We fastidiously look at your methods to ensure they meet safety requirements and observe business guidelines.
- Code Evaluation: Our consultants examine your supply code to identify safety flaws early in growth. This helps decrease the probabilities of points within the ultimate product.
Significance for Companies
Safety testing is essential for every type of companies. Listed below are the the explanation why:
- Information Safety: It helps maintain protected detailed data. This consists of private data, monetary particulars, and mental property.
- Compliance: Many industries have strict safety guidelines. Common testing helps your methods observe these guidelines. This helps keep away from costly fines and penalties.
- Buyer Belief: By displaying you care about safety, you assist construct and maintain prospects’ belief in your services.
- Price Financial savings: Discovering and fixing vulnerabilities early can save some huge cash. That is associated to potential breaches or if methods are down.
- Repute Administration: Robust safety measures shield your model. They assist maintain your organization’s repute protected in case of a cyber assault.
Widespread Vulnerabilities
Understanding the widespread issues is essential for good safety testing. A few of the most frequent points we face are:
- Injection Flaws: These let attackers add dangerous code to your system. This may put your knowledge in danger.
- Authentication Weaknesses: If authentication isn’t completed correctly, it could let unauthorized folks entry delicate data.
- Cross-Website Scripting (XSS): This flaw permits attackers so as to add dangerous scripts to internet pages utilized by different customers.
- Insecure Direct Object References: This occurs when an app reveals a reference to a personal object, like a file or database key.
- Safety Misconfigurations: These errors normally come from utilizing unsafe default settings or incomplete setups.
We at Binary Informatics concentrate on widespread weaknesses in software program by means of safety testing. This helps maintain your software program sturdy in opposition to potential threats. Our plan finds issues which might be already there and helps cease new points from arising. This manner, we offer sturdy safety to your digital belongings.
Learn Additionally: QA Automation Testing Providers: The Key to Software program Success!
Key Parts of Safety Testing Providers
At Binary Informatics, we all know that good software program safety testing providers embody a number of essential components. These components work collectively to create sturdy safety in opposition to potential threats and weaknesses. Let’s have a look at the principle components that help our safety testing providers.
Vulnerability Evaluation
Vulnerability evaluation is a cautious examine of safety issues in an data system. We do that essential course of to see if a system has any recognized weaknesses. We additionally rank how severe these weaknesses are and counsel methods to repair or scale back the dangers when wanted.
Our course of for vulnerability evaluation has 4 primary steps:
- Testing: We create an in depth listing of an software’s vulnerabilities by utilizing automated instruments and handbook strategies.
- Evaluation: We discover the place the vulnerabilities come from and what causes them throughout testing.
- Evaluation: We rank the vulnerabilities to resolve which of them are extra severe. We take into account elements like affected methods, knowledge in danger, and potential influence.
- Remediation: We be a part of forces with safety, growth, and operations groups. Collectively, we resolve the easiest way to repair every vulnerability.
To provide a whole overview, we use completely different sorts of vulnerability assessments:
| Evaluation Sort | Description | |
| Host evaluation | Evaluates essential servers for potential vulnerabilities | |
| Community and wi-fi evaluation | Examines insurance policies and practices to stop unauthorized entry | |
| Database evaluation | Identifies vulnerabilities in databases and massive knowledge methods | |
| Utility scans | Detects safety vulnerabilities in internet purposes and their supply code |
Penetration Testing
Penetration testing, or pen testing, is a authorized observe the place consultants examine how protected a pc system is by simulating an assault. At Binary Informatics, our testers use the identical instruments and strategies as actual attackers. They establish and present how weak spots within the system can have an effect on the enterprise.
We normally observe these steps in our penetration testing course of:
- Reconnaissance: Gather details about the goal from each private and non-private sources.
- Scanning: Test the goal for any weaknesses utilizing particular instruments.
- Gaining entry: Discover the most effective instruments and strategies to enter the system.
- Sustaining entry: Fake to remain linked lengthy sufficient to satisfy the attacker’s objectives.
Our penetration testing providers discover completely different areas, akin to:
- Internet purposes
- Cell purposes
- Networks
- Cloud environments
- Containers
- Embedded units (IoT)
- APIs
- CI/CD pipelines
Code Evaluation
Safe code overview is the cautious examine of software program supply code. Its goal is to search out and repair safety vulnerabilities. At Binary Informatics, we see this as an essential step within the software program growth life cycle (SDLC).
Our code overview course of entails:
- Make a safe coding coverage so builders know what to observe.
- Train builders about protected coding strategies.
- Use steady integration and steady deployment (CI/CD) that features safety checks.
- Ceaselessly examine and replace our strategies to maintain up with new safety traits and threats.
We use each handbook and automatic instruments for code overview.
- Static Utility Safety Testing (SAST) instruments have a look at supply code with no need to run this system.
- Dynamic Utility Safety Testing (DAST) instruments examine purposes whereas they’re operating.
- Interactive Utility Safety Testing (IAST) instruments combine options from each static and dynamic testing.
- Software program Composition Evaluation (SCA) instruments look at the components of an software for recognized vulnerabilities.
At Binary Informatics, we embody key components in our safety testing providers. This manner, we offer a full methodology for recognizing and lowering potential safety dangers in your software program methods.
The Safety Testing Course of
At Binary Informatics, we have now a transparent methodology for our software program safety testing providers. This course of helps us cowl all areas and discover vulnerabilities successfully. Let’s discover the essential steps in our safety testing course of.
Planning and Scoping
We begin by setting clear objectives and defining what the evaluation will cowl. This essential step helps direct the entire testing course of and makes positive we meet your group’s safety wants. Some widespread objectives may embody:
- Test the safety of sure apps.
- Discover vulnerabilities in community methods.
- Take a look at how nicely safety measures work.
To make sure a clean testing course of, we:
- Inform our pen check staff what they should know in regards to the goal surroundings.
- Get written permission from the appropriate folks so we keep authorized and moral.
- Create a transparent check plan that lists the actions, methods, and instruments we’ll use.
We select the appropriate testing methodology that matches your objectives and wishes. Some widespread strategies are:
- Black field testing: Acts like an out of doors attacker who is aware of nothing in regards to the system.
- White field testing: Requires a powerful understanding of the system’s inside options.
- Grey field testing: Is in the course of black and white field testing.
Execution
In the course of the execution section, we use a number of strategies. We mix handbook testing, exploring vulnerabilities, and simulating assaults. This helps us discover vulnerabilities and examine how nicely the safety measures work.
Our course of for getting issues completed normally consists of these steps:
- Reconnaissance: We gather details about the goal methods, networks, or purposes. We use each passive and lively information-gathering strategies. This may embody open-source intelligence (OSINT) instruments.
- Scanning and Discovery: We discover open ports and have a look at community visitors with instruments like Nmap. This lets us see the place attackers may get in.
- Vulnerability Evaluation: We fastidiously examine for potential weaknesses within the goal methods and purposes. This consists of:
1. Utilizing automated instruments
2. Making use of handbook testing methods
3. Checking configuration settings
Reporting and Remediation
After we end the execution section, we then go to reporting and fixing points. This half is essential. It provides helpful data and helps to make your group’s safety higher.
Our reporting and remediation course of consists of:
- Documentation and Evaluation: We write down all of the vulnerabilities we discover. We be aware their influence and the dangers related to them. We classify our findings by how severe they’re and the way possible they’re to be exploited. This helps us resolve which points to repair first.
- Complete Report Preparation: We put collectively an in depth report that features:
- A abstract for executives
- Detailed findings
- Solutions for fixing issues
- Clear steerage on the right way to prioritize vulnerabilities based mostly on seriousness
- Sensible steps to cut back the dangers we’ve recognized
- Remediation Help: We staff up together with your employees to repair the vulnerabilities discovered. This might imply making use of safety updates, altering system settings, or including further safety measures.
- Verification and Retesting: As soon as we end fixing the problems, we examine once more to ensure every little thing is solved. This step is essential as a result of it exhibits that our actions labored and that no new issues have appeared.
By utilizing this clear safety testing course of, we at Binary Informatics examine your methods fastidiously. We provide the data it is advisable enhance your safety.
Learn Additionally: Offshore Software program Testing: A Price-Efficient Resolution for Your QA Wants
Instruments and Applied sciences for Safety Testing
At Binary Informatics, we all know how essential it’s to make use of the most effective instruments and applied sciences. This helps us present sturdy safety testing providers. We use varied options to search out vulnerabilities, examine dangers, and maintain our shoppers’ digital belongings protected from safety threats. Let’s have a look at the principle instruments and applied sciences we use for our safety testing.
Open Supply Instruments
We use a number of sturdy open-source instruments to enhance our safety testing abilities.
- OWASP ZAP (Zed Assault Proxy): This software is nice for automated scans and helps with handbook safety testing of internet purposes. It’s simple to make use of, even for individuals who are new to safety testing.
- SQLMap: We use this software, based mostly on Python, to search out and reap the benefits of SQL injection vulnerabilities in databases. It really works with a number of database providers like MySQL, Oracle, and Microsoft SQL Server.
- Wapiti: This software permits us to scan internet purposes from the skin, discovering vulnerabilities with out trying on the supply code.
- OpenVAS: We use this scanner to examine servers and community units. It seems for open ports, misconfigurations, and potential safety weaknesses.
- Vega: This scanner, made with Java, helps us discover vulnerabilities like SQL injection, cross-site scripting, and unintentionally revealed delicate data.
These open-source instruments give us the possibility to vary our testing methodology. We are able to modify it to satisfy the wants of every mission.
Industrial Options
We use many open-source instruments in our work. Nonetheless, we additionally use industrial options to enhance our safety testing capabilities.
- Netsparker: This easy-to-use software provides very correct outcomes. It finds over 1,000 vulnerabilities, like SQL injection and cross-site scripting. A particular function checks discovered vulnerabilities routinely, saving us time on handbook checks.
- Acunetix: We use this software for computerized penetration testing. It finds and reviews greater than 4,500 internet software vulnerabilities. It might probably crawl hundreds of pages with out stopping, which is nice for large initiatives.
- Invicti: This scanner is ideal for companies. It combines dynamic (DAST) and interactive (IAST) scanning. This offers us full vulnerability protection and exact menace detection.
- Snyk: We use this safety platform geared for builders. It routinely finds vulnerabilities in code, open-source dependencies, containers, and infrastructure as code.
These industrial options add to our open-source toolkit. They provide superior options and help. This makes them supreme for safety testing at a enterprise degree.
Rising Applied sciences
To maintain up with altering cyber threats, we at all times search for and add new applied sciences to our safety testing processes.
- AI and Machine Studying: We’re utilizing sensible AI and ML instruments to take a look at massive quantities of knowledge. These instruments assist us discover patterns and spot issues higher. This tech improves our capability to guess the place assaults may come from and offers concepts for fixing them.
- DevSecOps Integration: We’re including safety checks in each step of growth. This manner, safety is a part of the event course of, not only a last-minute thought.
- Container Safety Testing: As container use grows, we’re creating particular exams to examine the safety of containers. We want to ensure they’re separated, arrange appropriately, and free from issues.
- API Safety Testing: With APIs turning into essential in at the moment’s apps, we’re specializing in particular exams for API safety. This protects in opposition to widespread issues like injection assaults and knowledge leaks.
- Serverless Safety Testing: As extra firms change to serverless computing, we alter our testing strategies to cope with the particular safety points this creates. We concentrate on discovering misconfigurations and managing permissions.
At Binary Informatics, we mix instruments, expertise, and new traits. This manner, we offer full and efficient software program safety testing providers. Our strategy retains companies protected in opposition to fast-changing threats. It helps them preserve sturdy safety in a fancy digital world.
Challenges in Software program Safety Testing
At Binary Informatics, we all know that safety testing providers face many challenges. These challenges come from a number of elements. They have an effect on how nicely and how briskly safety testing works.
Evolving Menace Panorama
We’ve seen a giant rise in advanced cyberattacks geared toward essential infrastructures and huge organizations. The dangers are at all times shifting, as expertise is rising shortly and hackers are altering their approaches. For instance, the expansion of synthetic intelligence (AI) has allowed cybercriminals to assault extra simply, even when they’ve much less expertise or sources.
Latest reviews say that menace actors launched round 11.5 assaults each minute throughout completely different industries. The healthcare and monetary sectors are a few of the most focused. The rationale for that is that these industries have useful data. This consists of checking account particulars, private identification data (PII), and Social Safety numbers. Cybercriminals discover this data very interesting.
We’ve observed that authorities teams entice cybercriminals. These criminals have causes associated to cash or international occasions. Crucial infrastructure can also be focused usually. It is because extra digital methods are open to new dangers.
Advanced Utility Architectures
Fashionable internet purposes might be quite simple or very advanced. Some are simply small scripts operating on one server. Others might be sophisticated, utilizing many methods, languages, and components. This complexity creates particular challenges for safety testing.
We see a number of forms of architectural fashions. Every mannequin wants a unique manner of testing.
- Platform-as-a-Service (PaaS): On this mannequin, the appliance proprietor can not entry the essential construction. This limits how they’ll repair issues straight.
- Serverless: This mannequin is nice for microservice-based setups. It runs single features as an alternative of bigger internet purposes.
- Microservice-based Structure: These purposes include a number of separate providers. They usually run in containers and use completely different working methods and languages.
We additionally want to consider issues like reverse proxies, load balancers, and Content material Supply Networks (CDNs). These can actually have an effect on how we do testing. Firewalls and Internet Utility Firewalls (WAFs) make safety testing much more sophisticated.
Useful resource Constraints
We all know that each one software program growth initiatives have limits on sources. That is true for companies of any dimension or revenue degree. These limits can enormously have an effect on the safety testing course of.
Vital useful resource limits we normally see are:
- Time: A short while to check could make groups really feel rushed. This may result in lacking essential vulnerabilities.
- Funds: A decent finances can restrict the usage of superior safety testing instruments or reaching out to expert safety professionals.
- Experience: There are sometimes extra jobs for expert cybersecurity folks than there are certified employees. This makes it onerous for organizations to guard their operations nicely.
- Expertise: Outdated methods, the boundaries of chosen applied sciences, and compatibility points can add extra challenges to the testing course of.
To unravel these issues, we at Binary Informatics plan early and clearly. We talk nicely and work collectively as a staff. And concentrate on a very powerful options too. We handle dangers and use expertise and instruments to be extra environment friendly, even with restricted sources.
Greatest Practices for Efficient Safety Testing
At Binary Informatics, we all know that sturdy safety testing is essential to guard software program purposes. We’ve discovered some primary methods that may enormously enhance how nicely safety testing works.
Steady Testing
We consider that testing ought to occur on a regular basis to maintain excessive safety requirements in software program growth. Once we add testing at each step, from growth to deployment, safety turns into a key a part of the method, not simply an afterthought.
Steady testing presents a number of advantages:
- Scalability: Automated steady testing helps us deal with large methods nicely. We are able to run hundreds of exams on the similar time on completely different platforms.
- Consistency: Automated exams run the identical manner every time. This offers us regular outcomes and confirms that vulnerability patches are working.
- Velocity: We are able to shortly examine new codes or adjustments. This helps us discover vulnerabilities quick in order that growth doesn’t decelerate.
- Price-effectiveness: At first, automated instruments appear pricey. Nonetheless, they save some huge cash in the long term by recognizing and fixing vulnerabilities early in growth.
Shift-Left Strategy
We help a shift-left strategy. This implies we deliver safety practices ahead within the software program growth life cycle (SDLC). This methodology matches with DevSecOps concepts. It locations safety at each stage of growth.
Key advantages of the shift-left strategy embody:
- Detecting vulnerabilities early helps lower down the probabilities of costly safety points later in growth or after the software program is stay.
- Higher software program design occurs as a result of groups are extra conscious of safety wants proper from the beginning of a mission.
- A lift in safety consciousness throughout the group occurs as builders find out about safety greatest practices.
- Begin by involving everybody early within the course of.
- Encourage staff members to share their concepts and suggestions.
- Deal with discovering and fixing points sooner moderately than later.
- Make use of instruments and strategies that assist in recognizing issues shortly.
- Preserve communication open and common amongst all staff members.
- Prepare the staff on the right way to spot points early of their work.
- Evaluation the method usually to see if enhancements might be made.
- Rejoice successes to maintain the staff motivated.
- Train builders the appropriate safety practices and instruments.
- Choose safety champions in growth groups to unfold consciousness and assist with communication.
- Encourage teamwork between growth, operations, and safety groups through the software program growth life cycle (SDLC).
- Arrange and use safe coding requirements that suit your group’s expertise wants.
Automation Integration
We see how essential automation is in bettering safety testing. Utilizing automated safety testing instruments within the CI/CD pipeline helps us do common and environment friendly safety checks all by means of the event course of.
Advantages of automation integration embody:
- We elevated check protection by pushing for extra safety testing in growth.
- We made safety controls the identical in numerous settings to decrease the possibility of human error.
- We lower down suggestions loops, which helps us discover and repair safety issues sooner.
To successfully combine automation, we advise:
- Use automated safety testing instruments that simply work with builders’ routines.
- Present safety coaching and consciousness packages with interactive programs and observe workouts.
- Arrange a powerful system for managing vulnerabilities to search out and prioritize safety issues throughout growth.
By utilizing these greatest practices, we at Binary Informatics assist organizations create software program that’s each protected and environment friendly. We concentrate on steady testing, a shift-left strategy, and automation integration. These strategies enhance the safety of purposes and encourage everybody concerned in growth to concentrate on safety.
Selecting the Proper Safety Testing Companion
At Binary Informatics, we all know that selecting the correct safety testing associate is essential for shielding your digital belongings. We’ve discovered some key factors to consider when making this large choice.
Experience and Expertise
We predict {that a} associate’s abilities and expertise are essential. It’s best to discover a firm that has a historical past of doing thorough safety assessments. The most effective associate ought to have:
- A bunch of educated consultants who’ve certifications like CISSP, CSSLP, OSCP, ECSA, LPT (Grasp), and CEH.
- They’ve expertise in your business, particularly should you work in strict fields like healthcare or finance.
- They know quite a bit about completely different testing strategies, akin to SAST, DAST, and SCA.
You will need to examine how they do their testing. We propose selecting an organization that makes use of human-led penetration testing as an alternative of simply automated instruments. Automation is helpful, but it surely can not present the insights and creativity that expert safety consultants deliver.
Service Choices
When selecting a safety testing associate, it’s essential to search out one that gives all kinds of providers. supplier ought to have:
- Vulnerability Scanning
- Penetration Testing
- Internet Utility Safety Testing
- Community Safety Testing
- Wi-fi Safety Testing
- Social Engineering Testing
- Compliance Testing
Moreover, take into account whether or not they present:
- Discover all internet purposes in your system with simple software discovery instruments.
- Use highly effective options to attach with IDEs, bug-tracking instruments, and code administration methods.
- Get help to assist builders see and repair vulnerabilities.
- Be part of coaching packages to find out about safety consciousness and protected coding practices.
Certifications and Compliance
We at Binary Informatics perceive how essential certifications and compliance are within the safety testing area. While you search for potential companions, take into consideration these factors:
- Related business certifications present their ability and dedication to greatest practices.
- They observe business requirements and guidelines which might be particular to your area, like HIPAA for healthcare.
- They’ll carry out exams that meet regulatory wants.
It’s essential to take a look at how nicely they report data. Ask for a pattern report. This manner, you may examine if it provides helpful insights in a easy and clear manner. It must be simple to grasp for each technical and non-technical folks.
Lastly, examine the associate’s repute within the cybersecurity area. Search for evaluations and ask for references. Take into consideration their historical past of success in earlier work. safety testing associate must be open about their methodologies. They need to even be able to reply any questions you could have about their providers.
By excited about these essential elements – abilities and expertise, providers offered, and certificates and guidelines – you may decide a safety testing associate. This may assist maintain your group’s digital belongings protected and guarantee sturdy safety.
Conclusion
Software program safety testing is essential. It helps shield digital belongings and retains buyer belief sturdy in at the moment’s altering menace surroundings. This information seems on the primary components, steps, and greatest practices for utilizing good safety testing providers. We cowl every little thing from discovering weaknesses to penetration testing. A whole strategy to safety testing is essential.
As companies cope with the tough space of cybersecurity, selecting the correct associate for safety testing is essential. This selection helps maintain their digital methods protected. By taking a look at elements like abilities, forms of providers, and guidelines, firms can select properly to enhance their safety. To additional shield your software program, get a quote for our safety testing providers. Take into account that spending on safety testing isn’t solely about stopping issues; it’s additionally about creating belief and reliability for your small business in at the moment’s digital world.
FAQs
1. What does safety testing entail within the context of software program testing?
Safety testing is a specialised type of software program testing geared toward assessing a system’s or software’s safety. Its main goal is to uncover vulnerabilities and threats, guaranteeing the system is safeguarded in opposition to unauthorized entry, knowledge breaches, and different security-related challenges.
2. What sort of software program safety testing requires handbook execution?
Penetration Testing, also known as Pen-Testing, entails simulating a real-time cyberattack on an software, system, or community inside a managed surroundings. Any such testing should be carried out manually by a talented and licensed safety skilled to precisely assess the effectiveness of safety measures.
3. At what stage of growth ought to safety testing be carried out?
Safety testing must be built-in early within the software program growth lifecycle. Conducting safety testing solely after the software program has been executed and deployed can result in considerably larger prices and problems.
4. What’s the objective of integration testing in software program growth?
Integration testing is a kind of software program testing that ensures completely different parts and methods inside an software work together appropriately. As an example, it could contain testing the communication with a database or verifying that microservices operate collectively as meant.