
Software safety posture administration firm Apiiro at present has launched two open-source instruments to assist organizations defend towards malicious code of their functions. The motion comes on the heels of Apiiro’s safety analysis that reveals hundreds of malicious code cases in repositories and packages.
In response to the corporate, its focus within the analysis was deep code evaluation and analyzing malicious samples for patterns to search out methods to defend towards malicious code. “Malicious code is without doubt one of the most accessible and easy-to-execute assault vectors,” the corporate wrote in a weblog concerning the analysis. “The safety of dependency managers and supply code internet hosting platforms remains to be evolving, with giant gaps in areas like human-to-digital identification verification, supply and launch validation, and extra. Main safety gaps additionally exist in construct methods, artifact managers, and pipeline instruments.”
Malicious code is launched by way of anti-patterns, the analysis discovered, and obfuscated code is a key anti-pattern. A second anti-pattern is naive code execution, beneath which the code is obtained as information and executed on the fly, with none alternative to scan it previous to supply.
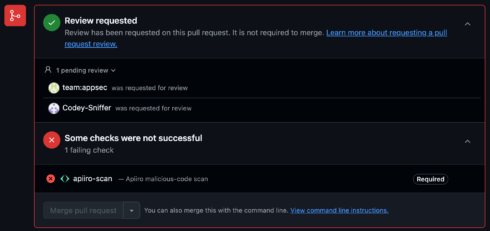
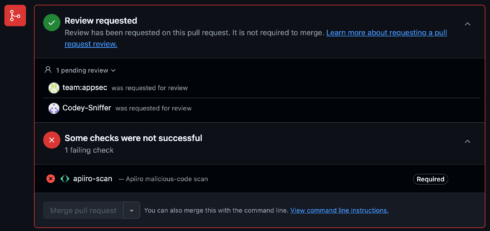
The analysis discovered that the introduction of malicious code may be detected a majority of the time utilizing the brand new open-source instruments the corporate is releasing at present. The primary is PRevent, which the corporate described as “an open-source app for scanning pull requests occasions, notifying you of suspicious code, and providing seamless integration, excessive configurability, and important orchestration options.”
The second open-source software launched at present is a malicious code detection ruleset to run on Semgrep, which has been forked by Opengrep after the previous determined to maneuver its engine onto a proprietary license as that firm appears to monetize components of the challenge.
Apiiro means that one of the best place to forestall malicious code from getting into the codebase is thru use of a pre-merge hook, which it defined is “triggered by pull request occasions by way of webjooks and managed by strictly permissioned entities.” PRevent can kick off code critiques and even block merges till a scan passes or a reviewer grants approval.
Extra on Opengrep
The Semgrep challenge has been round since 2017, and is broadly used within the trade. Its two parts are the pattern-matching OSS Engine and OSS Guidelines, a shared repository of guidelines created by Semgrep and open for contributions from the group.
In December 2024, Semgrep introduced modifications to the OSS Engine license, taking it behind a business license, in impact eradicating that crucial piece from the open supply group. One of many issues Semgrep did was to remove JSON and Serif, a format for outputting outcomes from the OSS Engine, in line with Varun Badhwar, founder and CEO at Endor Labs, which is one in every of greater than 10 corporations which have created the Opengrep fork. “The writing is on the wall to vary the identify from open supply to Group Version,” he stated. “We predict the Semgrep OSS Engine is all too essential for it to be now within the fingers of 1 firm to find out the long run.”
Organizations that create open supply after which change their licenses – for any variety of causes – it’s normally for monetary causes. Ann Schlemmer, CEO at open supply database firm Percona, stated that “By doing so, they’re breaking the group’s belief and undermining what open supply is supposed to be.”
“What I might quite see is individuals being as clear as they’ll,” she added. “In the event you consider in your challenge that you simply’ve accomplished, and also you additionally wish to proceed so as to add worth, then be unapologetic about going open core, or deciding what you will give to the group beneath that open supply license, after which what you will maintain again. Your IP is your IP, however in case you put one thing out beneath an open supply license, it’s very nicely outlined. It’s sort of everyone’s IP at that time.”
Badhwar famous that the businesses behind the Opengrep fork are solely momentary stewards of the challenge. “We’ve very clearly dedicated publicly that we’re simply as an interim [group] organizing this long run. We wish to hand this over to a basis to run.” He stated the businesses haven’t but decided which basis could be most acceptable, however added, “We’ve already collectively come collectively and invested in hiring full-time engineers to work on this engine. Our objective is to convey again, on the very least, every part that Semgrep took away in December’s announcement, however extra importantly, put in much more funding on efficiency, on compatibility with Home windows, for instance, with eradicating a few of the restrictions on multi-file evaluation that it has within the open supply version.”
Schlemmer thinks this transfer to place open-source tasks into foundations goes to be a pattern. “If corporations have a very fashionable open supply challenge that’s broadly used, after which they resolve they wish to change their license — once more, financial causes, no apologies for any individual earning profits off of what they’ve put out – operating to the foundations, I feel, is a option to be sure that we preserve belief in open supply, and still have a sustainability of a extremely standard challenge.”